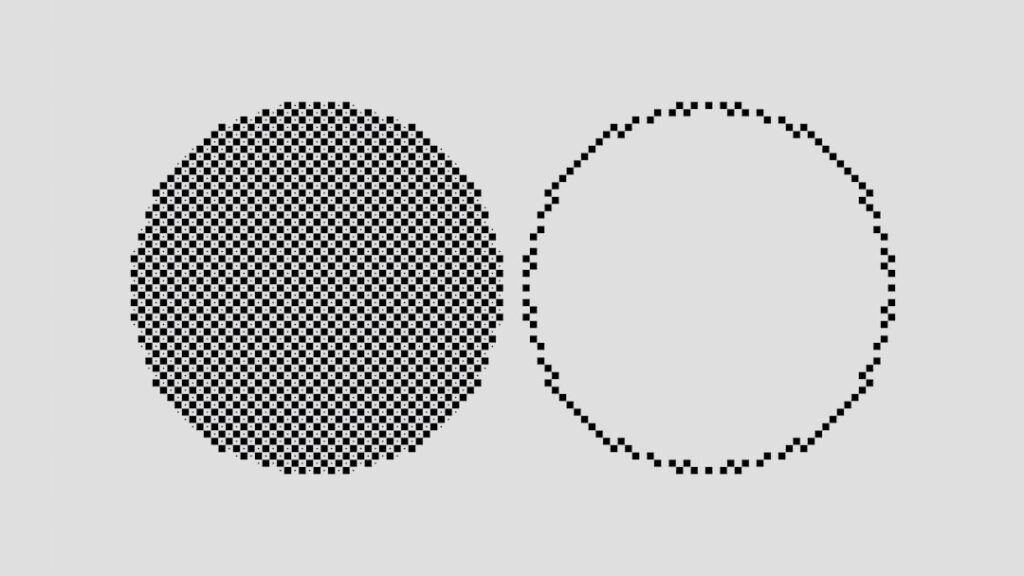
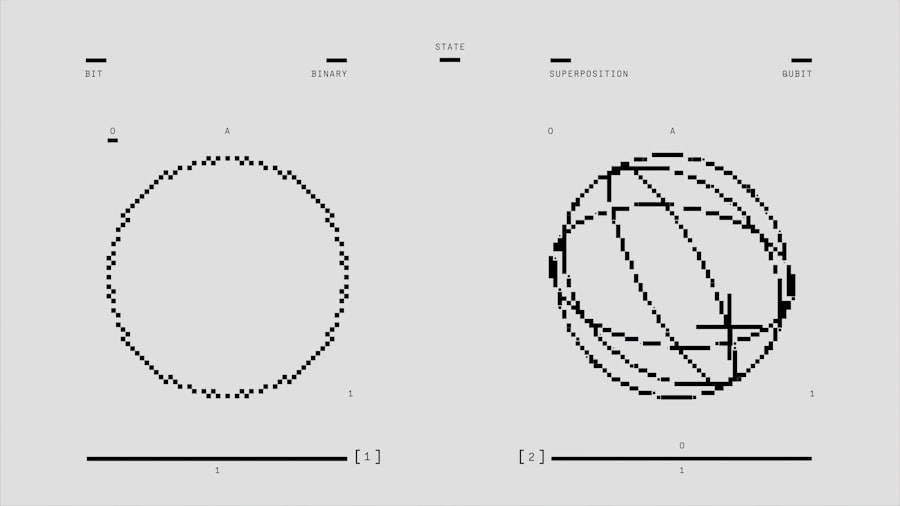
Quantum computing represents a paradigm shift in the way we process information, leveraging the principles of quantum mechanics to perform calculations at unprecedented speeds. Unlike classical computers, which use bits as the smallest unit of data, quantum computers utilize quantum bits, or qubits. Qubits can exist in multiple states simultaneously due to a property known as superposition.
This allows quantum computers to process a vast amount of possibilities at once, making them particularly powerful for certain types of computations. For instance, while a classical computer might need to evaluate each possible solution to a problem sequentially, a quantum computer can explore many solutions simultaneously, drastically reducing the time required for complex calculations. Entanglement is another fundamental principle of quantum mechanics that enhances the capabilities of quantum computing.
When qubits become entangled, the state of one qubit becomes dependent on the state of another, regardless of the distance separating them. This interconnectedness allows for more complex operations and can lead to faster processing speeds. The combination of superposition and entanglement enables quantum computers to tackle problems that are currently intractable for classical systems, such as factoring large numbers or simulating molecular interactions in chemistry and materials science.
As researchers continue to explore the potential of quantum computing, they are uncovering new algorithms and applications that could revolutionize various fields.
The Limitations of Classical Computing
Classical computing, while powerful and versatile, is constrained by several inherent limitations that become increasingly apparent as computational demands grow. One significant limitation is the reliance on binary logic, where data is represented as either a 0 or a 1. This binary system restricts the amount of information that can be processed simultaneously.
As problems become more complex, classical computers often struggle with efficiency and speed, leading to longer processing times and increased energy consumption. For example, tasks such as optimization problems or large-scale simulations can take an impractically long time to solve using classical methods. Moreover, classical computers face challenges related to scalability and parallelism.
While advancements in hardware have led to faster processors and increased memory capacity, there are physical limits to how small transistors can be made and how many can be packed onto a chip. This phenomenon, known as Moore’s Law, suggests that the exponential growth in computing power will eventually plateau as we approach these physical limits. Additionally, classical systems are often hampered by issues such as heat dissipation and energy efficiency, which become more pronounced as computational demands increase.
As a result, researchers are actively seeking alternative computing paradigms, such as quantum computing, to overcome these limitations and unlock new possibilities.
Quantum Computing and Encryption
The intersection of quantum computing and encryption is a topic of significant interest and concern in the field of cybersecurity. Traditional encryption methods rely on mathematical problems that are difficult for classical computers to solve, such as factoring large prime numbers or solving discrete logarithms. These methods form the backbone of secure communications on the internet today.
However, quantum computers possess the potential to break these encryption schemes with relative ease due to their unique computational capabilities. One of the most well-known algorithms that highlights this vulnerability is Shor’s algorithm, which can factor large integers exponentially faster than the best-known classical algorithms. This means that a sufficiently powerful quantum computer could decrypt data protected by RSA encryption—a widely used standard for secure data transmission—within a matter of hours or even minutes.
The implications of this capability are profound; sensitive information such as financial transactions, personal communications, and government secrets could be exposed if quantum computers become widely available before adequate countermeasures are implemented.
The Threat to Modern Encryption
| Encryption Threat | Impact |
|---|---|
| Government Backdoors | Risk of unauthorized access to sensitive data |
| Quantum Computing | Potential to break current encryption algorithms |
| Misuse of Encryption | Challenge in balancing privacy and security |
The threat posed by quantum computing to modern encryption methods cannot be overstated. As quantum technology advances, the risk of exposure for encrypted data increases significantly. Current encryption standards like RSA and ECC (Elliptic Curve Cryptography) rely on the difficulty of certain mathematical problems for their security.
However, with the advent of quantum computing, these problems may no longer be insurmountable. For instance, while it may take classical computers thousands of years to factor a 2048-bit RSA key, a quantum computer equipped with Shor’s algorithm could potentially accomplish this task in mere hours. This looming threat has led to growing concerns among cybersecurity experts and organizations worldwide.
The realization that sensitive data could be compromised has prompted many entities to reassess their security protocols and consider transitioning to quantum-resistant encryption methods. The urgency is further amplified by the fact that much of the data transmitted today may remain sensitive for years or even decades; thus, it is crucial to implement robust security measures before quantum computers become mainstream. The challenge lies not only in developing new encryption algorithms but also in ensuring their widespread adoption across various sectors.
Quantum Computing Breakthroughs
Recent years have witnessed remarkable breakthroughs in quantum computing technology, propelling it closer to practical applications. Companies like Google, IBM, and Rigetti Computing have made significant strides in developing quantum processors with increasing numbers of qubits and improved coherence times—the duration for which qubits maintain their quantum state before decohering into classical states. For instance, Google’s Sycamore processor achieved “quantum supremacy” in 2019 by performing a specific calculation faster than the most advanced classical supercomputers could manage.
Moreover, advancements in error correction techniques have been pivotal in making quantum computing more viable. Quantum systems are inherently susceptible to noise and errors due to environmental interactions; thus, developing robust error correction codes is essential for reliable computations. Researchers are exploring various approaches to error correction, including surface codes and cat codes, which aim to protect qubits from decoherence while maintaining computational efficiency.
These breakthroughs not only enhance the performance of quantum computers but also pave the way for more complex algorithms and applications across diverse fields.
Securing Data in the Quantum Era
As we transition into an era where quantum computing becomes more prevalent, securing data against potential threats will require innovative approaches and strategies. One promising avenue is the development of post-quantum cryptography—encryption methods designed to be secure against both classical and quantum attacks. These algorithms leverage mathematical problems that remain difficult for quantum computers to solve, such as lattice-based cryptography or hash-based signatures.
Organizations are beginning to adopt post-quantum cryptographic standards in anticipation of future threats. The National Institute of Standards and Technology (NIST) has been actively working on evaluating and standardizing post-quantum cryptographic algorithms through its ongoing competition. By establishing robust standards for post-quantum cryptography, NIST aims to provide a framework for organizations to transition their security protocols effectively and ensure data integrity in a world where quantum computing is a reality.
The Race to Develop Quantum-Resistant Encryption
The race to develop quantum-resistant encryption is intensifying as both private companies and government agencies recognize the urgency of addressing potential vulnerabilities posed by quantum computing. Researchers are exploring various cryptographic techniques that could withstand attacks from quantum algorithms like Shor’s algorithm. Lattice-based cryptography has emerged as a leading candidate due to its strong security foundations and efficiency in both key generation and encryption processes.
In addition to lattice-based methods, other approaches such as code-based cryptography and multivariate polynomial equations are being investigated for their potential resilience against quantum attacks. The challenge lies not only in developing these algorithms but also in ensuring their practicality for real-world applications. Factors such as computational efficiency, ease of implementation, and compatibility with existing systems must be considered when evaluating potential candidates for post-quantum cryptography.
The Future of Quantum Computing and Encryption
Looking ahead, the future of quantum computing and encryption is poised for transformative changes that will reshape our digital landscape. As quantum technology continues to advance, we can expect an increasing number of applications across various sectors, from pharmaceuticals to finance and beyond. The ability to simulate complex molecular interactions could lead to breakthroughs in drug discovery, while optimization algorithms could revolutionize supply chain management.
Simultaneously, the evolution of encryption methods will play a critical role in safeguarding sensitive information in this new era. Organizations will need to remain vigilant in adopting post-quantum cryptographic standards while continuously assessing their security protocols against emerging threats. Collaboration between academia, industry, and government will be essential in fostering innovation and ensuring that robust security measures keep pace with technological advancements.
As we navigate this uncharted territory where quantum computing intersects with encryption, it is imperative that stakeholders remain proactive in addressing potential vulnerabilities while harnessing the transformative power of this groundbreaking technology. The journey toward a secure digital future will undoubtedly be complex but holds immense promise for enhancing our ability to protect data in an increasingly interconnected world.
FAQs
What is quantum computing?
Quantum computing is a type of computing that takes advantage of the strange ability of subatomic particles to exist in more than one state at any time. This allows quantum computers to perform complex calculations much faster than traditional computers.
How does quantum computing pose a threat to modern encryption?
Quantum computers have the potential to break modern encryption algorithms, such as RSA and ECC, by quickly solving the mathematical problems on which these algorithms are based. This could compromise the security of sensitive data and communications.
What are the implications of quantum computing breaking modern encryption?
If quantum computing were to break modern encryption, it could lead to a significant security risk for sensitive information, including financial transactions, personal data, and government communications. This could have far-reaching implications for privacy and security.
Are there efforts to develop quantum-resistant encryption algorithms?
Yes, there are ongoing efforts to develop quantum-resistant encryption algorithms that would be secure against attacks from quantum computers. These algorithms are designed to withstand the computational power of quantum computers and provide secure encryption for the future.
Is quantum computing a reality today?
While quantum computing is still in its early stages and not yet widely available for commercial use, significant progress has been made in developing quantum computers. Companies and research institutions are actively working on building more powerful and reliable quantum computing systems.